|
 |
|||||||
|
The strength of an encryption algorithm is related to two factors. One is the strength of the algorithm itself. The second is the size of the key used with the algorithm. The RC5 algorithm has been extensively examined by RSA Data Security, Inc. as well as outside consultants. The cryptographic community is confident that RC5 is a secure algorithm. The only way to break a secure algorithm is to try every possible key on a sequence of encrypted data. As the size of the key increases, the time and effort required to guess the correct key increases. Trying every possible key is known as a brute force attack. A key 8 bits long contains 256 possible keys. A brute force attack on this key would be simple. However, the number of possible keys increases exponentially with key size. A 56-bit key contains 256 possible keys. If an attacker tried one million keys a second, it would take 2285 years to try each one. A 64-bit key would take the same attacker 585,000 years. It is estimated that a million dollar parallel processing computer can crack a 128-bit key in 1018 years. It is important to evaluate the requirements for encryption. If the data being encrypted is time sensitive, shorter keys can be used. For example, if you are encrypting details of a planned merger, the data must be kept secret for a few months. If an attacker manages to decrypt the data 20 years after the merger is complete, whatever information is gained will be useless.
The RC5 Algorithm A detailed description of the RSA RC5 algorithm is available from RSA at http://www.rsa.com.
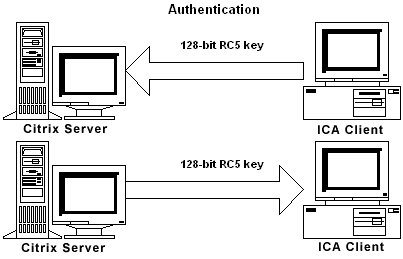
RC5 Keys During user logon, Secure ICA uses two 128-bit keys for enhanced security. One key is used to encrypt ICA packets the server sends to the client. The other key is used for client to server communication.
Generating RC5 Keys Each time a ICA client connects to a Citrix server the four RC5 keys are generated. The Diffie-Hellman algorithm is used when two people need to establish secret keys but they cannot securely transmit those keys to each other. The Citrix server and the ICA Client establish RC5 session keys using the Diffie-Hellman key agreement algorithm. The Citrix server periodically generates two numbers (A and B) using the Encryption Service installed by the Secure ICA Option Pack. These numbers are the Diffie-Hellman parameters.
The Citrix server and client follow the steps
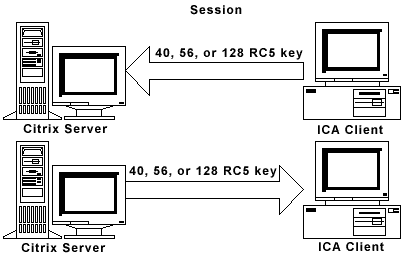
outlined below to establish a 1024-bit secret key. This secret key is split into two
128-bit keys used during logon and two 128-, 56-, or 40-bit keys used after logon.
The ICA client and Citrix server both have the same 1024-bit secret keys.
The mathematical steps to generate the secret
key are described below.
|
Secure ICA encryption is applied to the entire ICA packet. Except for a small encryption header, all of the ICA commands and data are encrypted, including:
|
||||||
|
||||||||